Are there any good WinDbg hiding plugins like OllyDbg's? Or a plugin that's open source and still in development for this purpose?
4 Answers
You can use ScyllaHide. There are plugins for many debuggers, but it is also possible to use InjectorCLI.exe to inject ScyllaHide into any process. Here are the steps (for a 32 bit process, if you want a 64 bit process, replace every x86 with x64):
- Extract ScyllaHide (download) anywhere;
- Run
NtApiTool\x86\PDBReaderx86.exeand when it's finished, copyNtApiCollection.inito the same directory asInjectorCLIx86.exe; - Open
ScyllaTest_x86.exewith WinDbg (x86) you should be inLdrpDoDebuggerBreak; - Execute
InjectorCLIx86.exe ScyllaTest_x86.exe HookLibraryx86.dll; - Run (F5) in WinDbg.
Without using ScyllaHide:
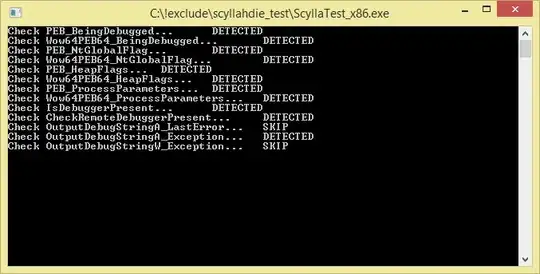
When using ScyllaHide:
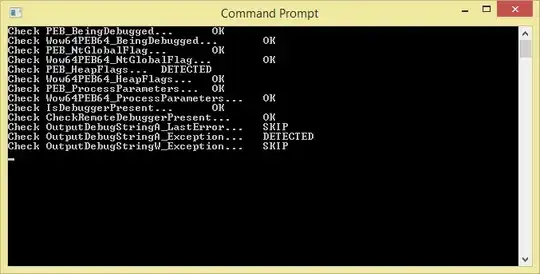
This process works for any debugger, if you feel like it you can even make an actual plugin for WinDbg. It should be quite easy.
I just added an option to inject to a process by process id. You can do this with:
InjectorCLIx86.exe pid:1234 HookLibraryx86.dll
- 1,652
- 10
- 19
-
While this does seem to work for usermode applications, I have to test the associated TitanHide (https://github.com/mrexodia/TitanHide/blob/master/README.md) for Kernel mode. ScyllaTest reports NtQuerySystemInformation_KernelDebugger: DETECTED – Kevin Dec 13 '17 at 20:06
-
Yes, ScyllaHide (and TitanHide for that matter) only work on usermode applications. – mrexodia Dec 14 '17 at 00:28
I am not sure if plugins exist but you can write simple scripts like below to hide WinDbg on case to case basis.
Peb->BeingDebuggedr?$t0 = (ntdll!_peb *) @$peb;?? @$t0->BeingDebugged;eb (@$t0+2) 0;?? @$t0->BeingDebuggedZwSetInformationThread(XP SP3 syscalls withsysenter)bp ntdll!ZwSetInformationThread "r eip = $ip+0n12 ; r eax = 0; gc"ZwQueryInformationProcesssyntax similar to
ZwSetInformationThreadin addition you would also need to fakeout DebugPort to NULL withed poi(ADDRESS) 0
Reading
- Peter Ferrie's "Ultimate" Anti-Debugging Reference
- 10,908
- 9
- 41
- 79
- 1,346
- 9
- 11
-
3ah, but anti-debugging is fraught with special cases - you can't arbitrarily zero the DebugPort, for example, without first checking the PID, in case the process is being debugged intentionally. Anyway, see my "Ultimate" Anti-Debugging Reference (pferrie.host22.com/papers/unp2011.htm) for a long list of tricks that you'd need to support (and some that you can't because they are direct kernel-returned data). – peter ferrie May 23 '13 at 16:01
-
-
@peterferrie thanks for the comment i wrote case to case basis just because i understand that there are lot of special cases anyway i have read your paper earlier quiet nice collection of antidebug tricks – blabb May 30 '13 at 18:47
I don't think such a plugin currently exists. However, if you're willing to implement a minimal windbg backend, you could extend uberstealth, which unfortunately I've never come to finish as a project (actually I think anti-debugging is a dead anyway, but that's another story ;-)). It's essentially IDAStealth, but with all debugger specific functionality factored out (there's a backend for IDA and Olly2). All you'd have to do is write a backend for Windbg (and fix the remaining bugs, I could help you with that though), all other code is debugger independent. Should be less than a few dozen lines of code.
- 1,183
- 7
- 18
-
Such a plugin indeed does not exist, but you don't need one either. See my answer (posting this comment in case the accepted answer doesn't change). – mrexodia May 31 '17 at 14:31
Here you can download QEMU virtual machine with embedded WinDbg stub: https://github.com/ispras/qemu/releases https://github.com/ispras/qemu/tree/windbg
This stub allows debugging with WinDbg without enabling Windows debugging mode.
- 21
- 2