The application I target has terribly annoying anti-debugging techniques. With x32dbg and ScyllaHide with the following configuration, the application exits immediately as soon as a breakpoint is hit, whether it is a software or hardware breakpoint.
The following are my settings:
A VEH debugger (I tried Cheat Engine) catches the exception. However, when it catches the exception, the Cheat Engine debugger shows the call stack as "empty" with a single setting showing 0x00000000 as the return address, so it's useless. However the exception code is 0xC0000005 so I know it's access violation.
What other anti-anti-debugging techniques can I use to get past the mechanism where the application crashes when a breakpoint gets hit?
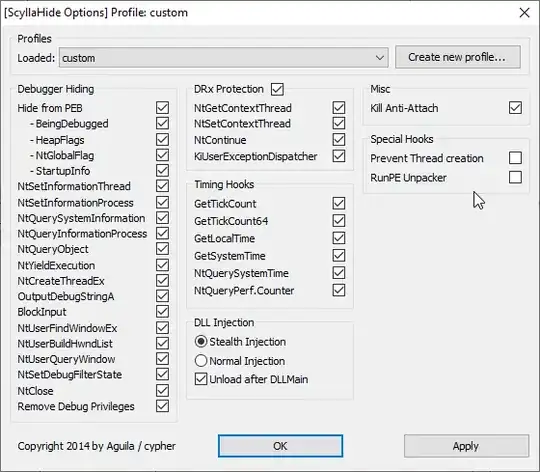
NtSetInformationThread, seems like it is being set with 0x11. Upon further investigating seems like it is caused by Themida (the sample was protected with it). I was able to debug by preventingNtSetInformationThreadas well as replacing several functions such asDbgUiRemoteBreakinandDbgUiBreakPointwith the original implementations, but then Themida itself seems to crash the sample and exit it abruptly. – shavit Apr 29 '20 at 07:16